Zero Trust Isolation with NIC Level Network Security Groups
This lab demonstrates a Zero Trust architecture in Azure by isolating a sensitive virtual machine within a shared subnet using a NIC-level Network Security Group. Whether you're building a secure dev environment or validating segmentation strategies, this lab offers a practical example.

The Goal
Demonstrate how to isolate a sensitive VM in a shared subnet using a NIC-level NSG.
The Lab
This lab is also available on YouTube
In this lab the following resources were used in Azure:
- A Resource Group.
- A Virtual Network (VNET) with Subnets.
- 2 Linux machines (VMs).
- Azure Bastion (a secure, fully managed service that provides private RDP/SSH access to virtual machines without exposing them to the internet).
- Network Security Group (NSG).
The Why
The ideal way to segment resources in Azure is to use separate subnets for resources that need to be grouped together. There are times however when resources exist in the same subnet and it may not be feasible to move them all into logical subnets.
In this situation there is a need to isolate resources in a subnet to improve security and limit who has access. This prevents unintended access and lateral movement with the virtual network.
The How
In another lab, Network Security Groups (NSGs) were used to control traffic to resources in different subnets. In this lab, 2 virtual VMs in the same subnet will be setup and will have connectivity to each other since they are in the same virtual network.
To isolate one VM, an NSG will be associated on its network interface card (NIC) as shown in the diagram:
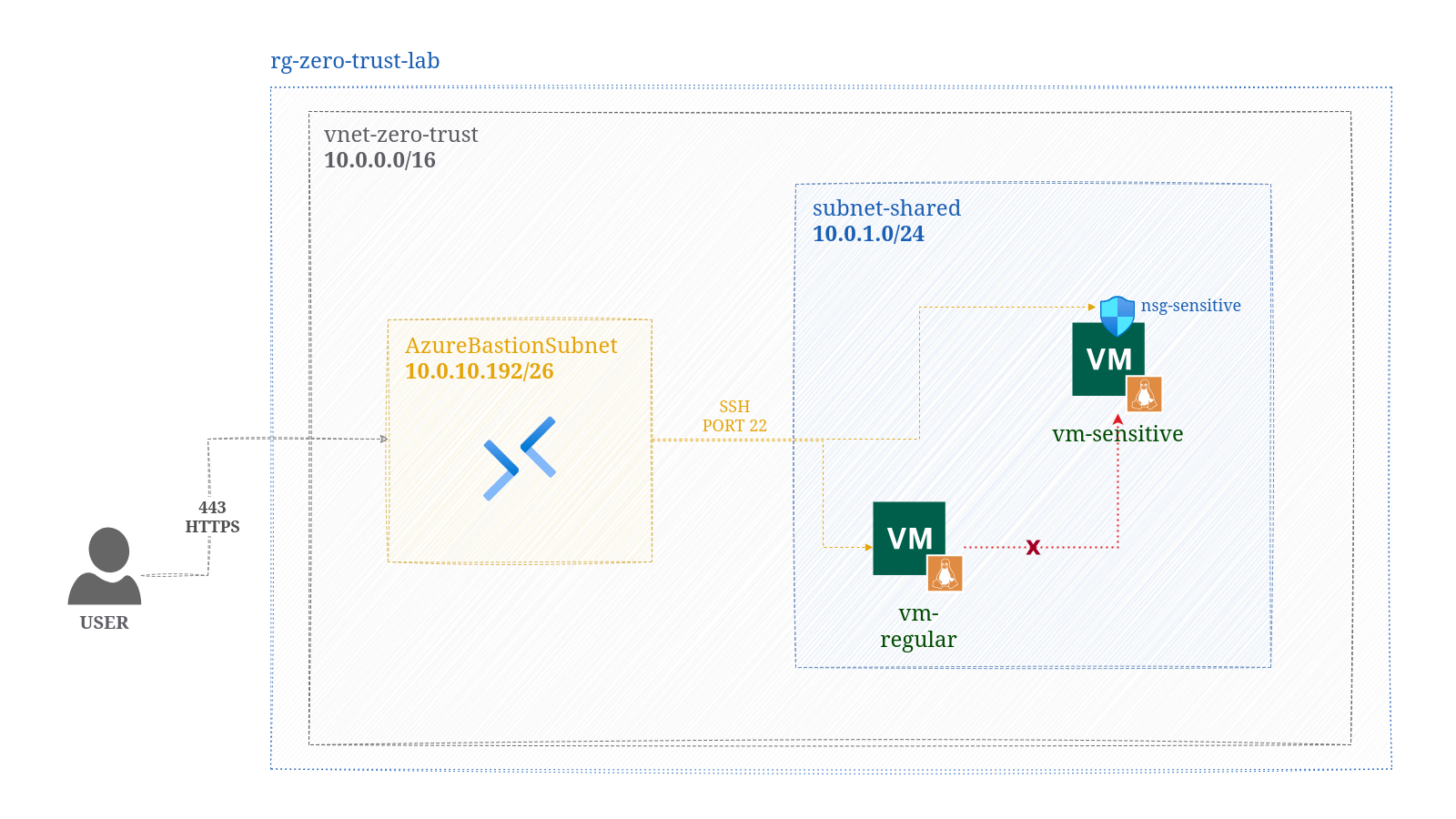
- vm-sensitive - represents a high value resource that needs to be secured.
- vm-regular - represents a standard workload resource that shouldn't have access to the high value resource.
Once the machines are setup, 2 rules are required on the NSG:
- Allow the Bastion subnet to access the vm-sensitive IP address over port SSH.
- Deny all other traffic.
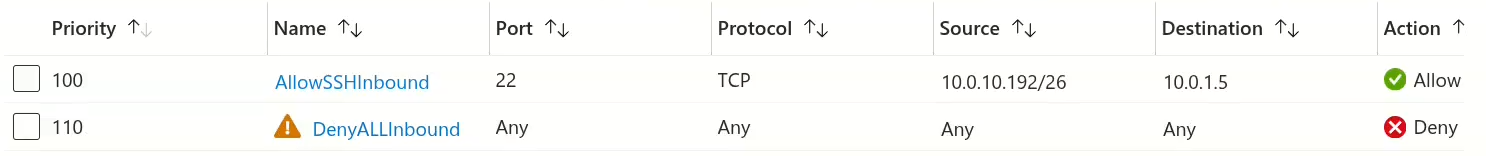
With the rules in place the following tests were performed to verify that vm-sensitive was isolated:
- Connect From Bastion to vm-sensitive.
- Use SSH to test connectivity from vm-regular to vm-sensitive:
ssh user@10.0.1.x
The SSH connection fails because it's blocked by the NIC level NSG
Using a VPN is a secure and simple way to protect your data.
The Results
In a Azure Virtual Network all resources can connect with each other.
With the NIC level NSG in place:
- Only Bastion was allowed to access vm-sensitive and only via SSH.
- vm-regular was unable to connect to vm-sensitive.
The Conclusion
This lab successfully demonstrated the use of a NIC level NSG to isolate a VM from a VM in the same subnet and virtual network.
In the real world this could be used to isolate VMs in an existing network from other VMs when it is not feasible to move VMs to new subnets or when the isolated VM requires access to resources in a subnet.
If you'd like to support my work, show your appreciation!



Comments ()