Micro-Segmentation with Application Security Groups
Application Security Groups (ASGs) provide an easy way to group together Azure resources like VMs and create simple to read NSG rules to control traffic between resources.

The Goal
Segment VMs on the same shared subnet using Application Security Groups (ASGs) to control outbound connectivity. Use ASGs to simplify the creation of Network Security Group (NSG) rules.
The Lab
This lab is also available on YouTube
In this lab the following resources were used in Azure:
- A resource group.
- A virtual network (VNET) with subnets.
- 3 Windows servers (VMs).
- Azure Bastion (a secure, fully managed service that provides private RDP/SSH access to virtual machines without exposing them to the internet).
- 3 Application Security Groups (ASGs)
- A Network Security Group (NSG).
The Why
When resources like virtual machines exist in the same subnet, Azure virtual networks allow full connectivity between subnets. There may however be a requirement to restrict access to VMs based on the services they provide. Typically this might be web apps or network shares that should not be accessible across departments.
One solution is to separate the VMs into their own subnets and associate NSGs (with custom rules) with each subnet, in fact this previous lab does exactly that. This involves creating subnets, managing multiple NSGs and rules, changes in VM IP addresses and downtime of services. For existing solutions, this represents a overhead of time, cost and redesign.
Instead ASGs can be used to segment VMs in the same subnet (also referred to as micro-segmentation). Using these can significantly simplify the rules to be created and the number of NSGs required.
The How
Three Windows server VMs are created in the same subnet and each are added to their own ASG. One NSG is associated with the subnet and rules are created referencing the ASGs.
The diagram shows the lab setup and the rules that will need to be configured:
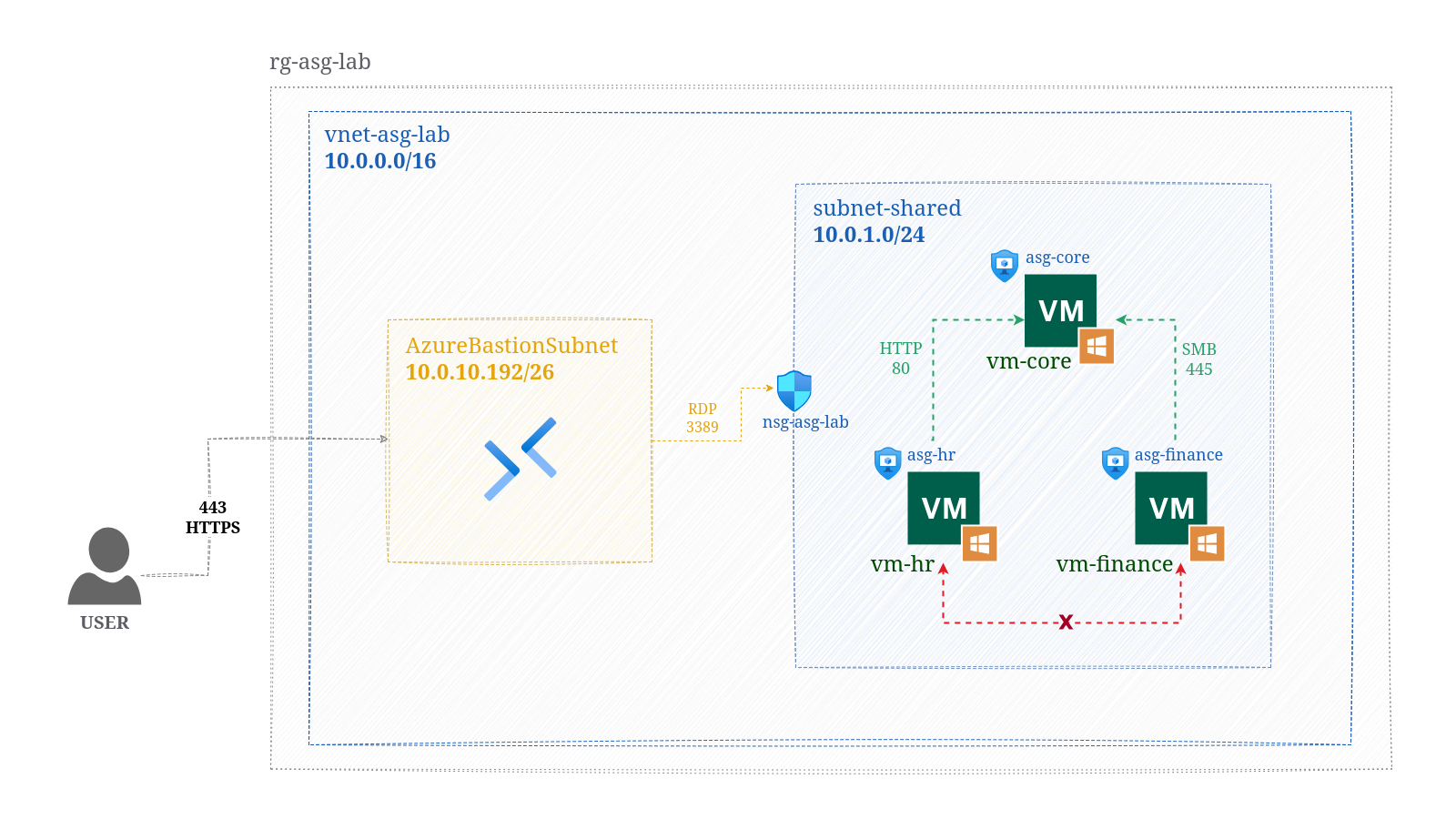
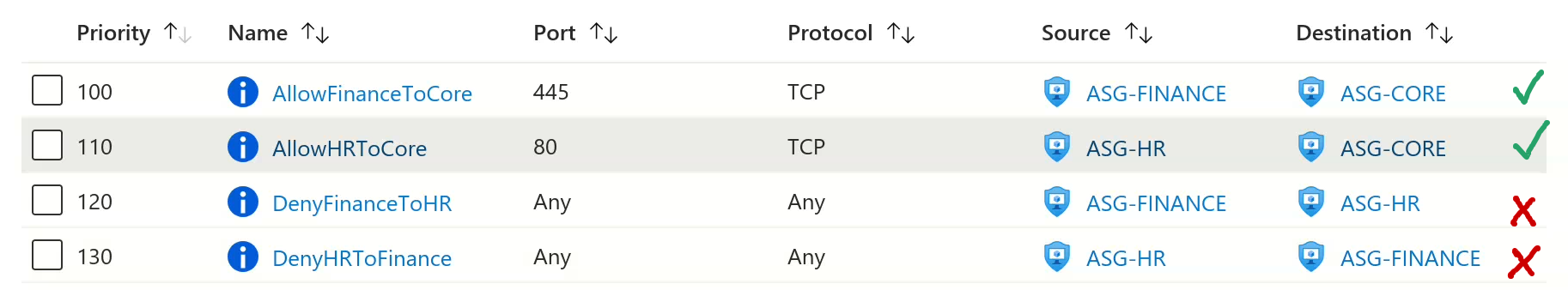
Rules created on NSG:
Using a VPN is a secure and simple way to protect your data.
The Results
PowerShell was used to successfully test connectivity using the IP addresses of the VMs and the port running the file sharing or web services:
- Test file sharing from
vm-financetovm-core
Test-NetConnection -ComputerName 10.0.1.x -Port 445
Result: Allowed
- Test connectivity from
vm-financetovm-hr
Test-NetConnection -ComputerName 10.0.1.x
Result: Blocked
- Test web from
vm-hrtovm-core
Test-NetConnection -ComputerName 10.0.1.x -Port 80
Result: Allowed
- Test connectivity from
vm-hrtovm-finance
Test-NetConnection -ComputerName 10.0.1.x -Port 445
Result: Blocked
The Conclusion
This lab successfully demonstrated ASG-based micro-segmentation in a shared subnet.
In practice ASGs allow flexibility when controlling traffic in an Azure virtual network, allowing for VMs to be subject to predefined NSGs rules by simply adding or removing the VMs in and out of ASGs.
If you'd like to support my work, show your appreciation!



Comments ()